








 Рейтинг: 4.3/5.0 (1840 проголосовавших)
Рейтинг: 4.3/5.0 (1840 проголосовавших)Категория: Windows: Сканеры, сниферы
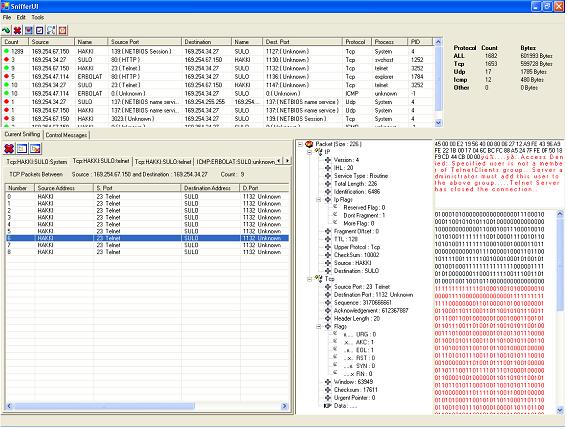
- Двойная схема: Java GUI управляет специальным ARM движком (без ТСРdump, нет Libpcap)
- Оптимизировано под вертикальную и горизонтальную ориентации
- Отображение информации о пакетах в реальном времени
- Параллельный захват пакетов на нескольких сетевых интерфейсов (Wi-Fi, 3G и т.д.)
- Гибкая фильтрация пакетов: типы протоколов / параметры, полезный текст
- Смешанный режим (некоторые адаптеры поддерживают его в открытых сетях)
- Уведомления о захвате пакетов (звук, вибрация, системные уведомления)
- Активные операции: отправка исходников, сканирование, просмотр, прокси, другие фишки
- Встроенный анализатор статистики пакетов
- Встроенный просмоторщик данных
- Встроенный root терминал
- Встроенный заметки пользователей
Вы не должны использовать приложения для незаконной деятельности. Используйте его только для образовательных или технических целей
М ануал по удалению проверки лицензии не работает выше v1.2.3
A software solution that comes as a powerful set of network visibility tools which allow you to perform an in-depth analysis data packets
Ultra Network Sniffer is a tool that allows you to investigate a network in order to obtain information about it and packet transfers. With it you are able to check-up on network performance, identify problems and resolve them.
It enables you to monitor transfers in real-time for multi network cards, as well as to track traffic from specific applications. Ultra Network Sniffer features dynamic network statistics and charting, HTML exporting capabilities, detailed traffic analysis, packet generating and much more.
It displays a comprehensive interface which makes it easy for you to access all its functions and features. It provides a ‘Connection Monitor’ section from where you can view all the automatically added monitoring targets, as well as add your own applications to track.
They are all made available in a hierarchical structure and you can toggle a monitoring session with a simple right click. It also offers plugins that work with Ethernet, IP, TCP, UDP, PPPOE, HTTP, FTP, WINS, PPP, SMTP and POP3 protocols.
Ultra Network Sniffer offers a ‘Protocol Packet Analyst’ tool that provides protocol statistics, as well as MAC and IP traffic statistics. Depending on your preferences, the arrangement of the window that houses this tool can be changed.
The application can also display packets that arrive from the wire, and allows you to choose which ones you want to send to the ‘Decoder’. The latter providing insight on the structure of the packets.
Ultra Network Sniffer comes with a ‘Packet Generator’ feature that allows you to edit and send packets through your network card. Just like all the other tools and features, this also grants easy access to its functions and makes the work process intuitive.
To improve workflow, the application makes it possible to color code each protocol you deal with, while also being able to enable or disable any one you want.
CURRENT VERSION: 1.30 build 0043 FILE SIZE: 1.9 MB DEVELOPER: GJPSoft RUNS ON: Windows All CATEGORY: C: \ Network Tools \ Protocol Analyzers/Sniffers LAST UPDATED ON: December 13th, 2004
Give Me Too - is an easy-to-use and affordable packet sniffer, network analyzer and network sniffer that plugs into computer networks and lets you easily monitor any Internet and e-mail activity that occurs in them.
Give Me Too captures all data transferred through the network via HTTP, FTP, SMTP, IMAP, POP3 and IRC protocols and lets you easily learn what your children, spouse or employees are doing online when you are not watching.
When this network sniffer works in the stealth mode, it is absolutely invisible even to the users of your computer. To unhide it, you need to press a custom keyboard shortcut.
All data captured by Give Me Too is stored to a folder of your choice and organized in the easy to navigate way (the captured Web pages and e-mail messages are sorted by protocol and computer or e-mail account). If you have several network cards installed, Give Me Too can simultaneously intercept packet sent through all these cards (up to 9 network interfaces are supported). Each interface can have individual settings.
The program features the powerful filtering system that let you capture specific information only. For example, you can capture only data coming from a specific URL, requested by a specific IP, or e-mails coming from a specific address. The network analyzer can work in the command line mode and also features the ability to analyze tcpdump files produced by other sniffers.
Supports: Windows XP only
Give Me Too ScreenshotsHere are 5 Best free network packet sniffers that does a fantastic job of packet sniffing. These free packet sniffer can analyze network packets of all outgoing traffic, and analyze information from them.
Before we go further, here is a definition of a Packet Sniffer from Wikipedia :
A packet analyzer (also known as a network analyzer, protocol analyzer or sniffer, or for particular types of networks, an Ethernet sniffer or wireless sniffer) is a computer program or a piece of computer hardware that can intercept and log traffic passing over a digital network or part of a network. As data streams flow across the network, the sniffer captures each packet and, if needed, decodes and analyzes its content according to the appropriate RFC or other specifications.
As mentioned in definition above, a packet sniffer is also able to sometimes decode and analyze network traffic to extract useful information. Such information could be passwords, or other credentials passed over network.
WireShark Packet SnifferWireshark is a free and open-source packet sniffer. This free network packet sniffer is one of the most popular packet sniffing freeware in the world. It is a cross-platform packet sniffer, and works on both Unix, as well as Windows.
One of the great feature of Wireshark packet sniffer is that it comes with a GUI that makes it extremely easy to use and setup. Apart from that, Wireshark website provides tons of resources, including videos, to learn how to use Wireshark, and analyze Wireshark data.
Sponsored Links
Wireshark packet sniffer is able to capture live real-time network packets. Apart from that, it is able to intelligently decipher packets based on their protocol. It can show the capture data on GUI. It is even able to detect and capture VOIP calls, and in some cases can even play back the media.
Wireshark is under active development, and is actively supported by a huge community of users and developers. This ensures that Wireshark is always kept up to date, and keeps coming out with new features.
Read more about Wireshark. or download free here .
Capsa Packet Sniffer FreeCapsa is a very comprehensive network packet sniffer that comes in both free version as well as paid version. Free version comes with tons of features, and is good enough for home use, as well as use in small business. Capsa does effective network analysis in real time by sniffing network packets, and analyze them. Free version of Capsa lets you monitor 50 IP addresses together, which makes this free packet sniffer especially useful for network administrators.
Capsa packet sniffer has been especially optimized for use in an enterprise. Some of the features include:
Download Capsa Packet Sniffer free here .
SniffPass Password SnifferSniffPass is a very specific type of packet sniffer that focuses on capturing passwords from network traffic. When you turn on Sniffpass password sniffer, it keeps on monitoring network traffic, and as soon as it intercepts a password, it instantly shows that on screen. This is a great way to find forgotten passwords of websites.
Sniffpass password sniffer is quite easy in its use, and provides a nice GUI to monitor all captured passwords. Sniffpass password sniffer supports most of the networks protocols, like: POP3, IMAP4, SMTP, FTP, and HTTP.
Microsoft Network MonitorMicrosoft Network Monitor is a free network packet sniffer. This works on Windows PCs, and provides expert capability to see all the network traffic in real time on an intuitive GUI. Microsoft Network Monitor is actively maintained by Microsoft, is available for a completely free download, and has a dedicated support site here. Microsoft Network Monitor can be used by beginners just to analyze their home network traffic, or by network administrators to analyze complete organization network by sniffing network packets.
This freeware packet sniffer supports more than 300 public, and Microsoft proprietary protocols. It even lets you capture wireless network packets.
Download Microsoft Network Monitor free here .
tcpdump is one of the oldest network packet sniffer. It was originally written in 1987! Tcpdump works primarily on Unix like operating systems, but there is a port of it that works on Windows as well. tcpdump is meant for experienced users only, as this packet sniffer is a command line utility. tcpdump can analyze network behavior, and monitor applications that generate network traffic.
Download tcpdump free here .
Another network monitor we covered earlier is iTrafficMonitor. If you want to analyze network packets of a particular web page, you can check out Fiddler. Also check out free offline browser .
PRTG Network Monitor is an advanced, professional tool for analyzing, maintaining and monitoring local networks. The program's free network sniffer captures the data passing through your network, analyzes this data and then presents it in a variety of easy-to-read formats.
PRTG Network Monitor is a useful tool for network administrators, security specialists, network application developers and anyone who needs a comprehensive picture of the traffic passing through their network connection or segment of a local area network.
You can use the network sniffer for data acquisition, connection & interface testing, diagnostic analysis, packet analyzer, identifying Shadow IT and more.
PRTG Network Monitor features a flexible system of fully configurable filters and reports that can be used to capture only the specific traffic patterns and network data you wish to analyze.
If you're looking for a professional tool that will simplify the tasks of monitoring and managing your network's traffic data, PRTG Network Monitor is your solution. Offering both a completely free, basic edition and expanded commercial editions, this free network sniffer is the right choice for all your network monitoring & analysis needs.
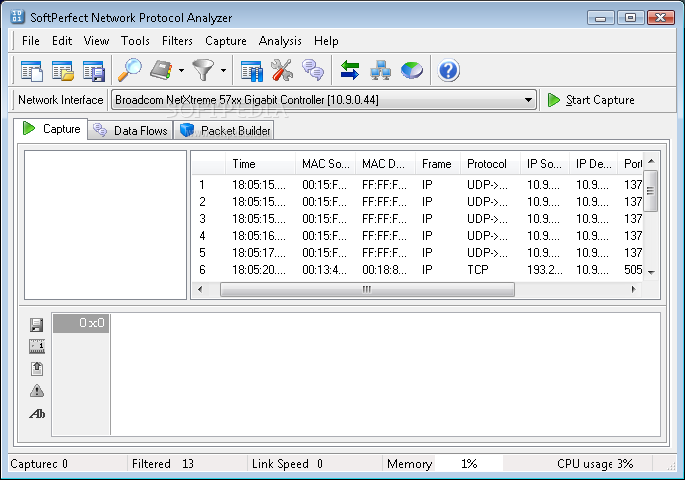
 SoftPerfect Network Protocol Analyzer is a free professional tool for analysing, debugging, maintaining and monitoring local networks and Internet connections. It captures the data passing through the dial-up connection or Ethernet network card, analyses this data and then represents it in a readable form.
SoftPerfect Network Protocol Analyzer is a free professional tool for analysing, debugging, maintaining and monitoring local networks and Internet connections. It captures the data passing through the dial-up connection or Ethernet network card, analyses this data and then represents it in a readable form.
This is a useful tool for network administrators, security specialists, network application developers and anyone who needs a comprehensive picture of the traffic passing through their network connection or a segment of a local area network.
SoftPerfect Network Protocol Analyzer presents the results of its analysis in a convenient and easily understandable format. It can defragment and reassemble network packets into streams. The program also features full decoding and analysis of network traffic based on the following low-level Internet protocols: AH, ARP, ESP, ICMP, ICMPv6, IGMP, IP, IPv6, IPX, LLC, MSG, REVARP, RIP, SAP, SER, SNAP, SPX, TCP and UDP. It also performs a full reconstruction of top-level protocols such as HTTP, SMTP, POP, IMAP, FTP, TELNET and others.
The flexible system of fully-configurable filters can be used to discard all network traffic except for the specific traffic patterns you wish to analyse. There is also a packet builder, which allows you to build your own custom network packets and send them into the network. You could use the packet builder feature to check the network’s protection against attacks and intruders.
This is now a discontinued software product. There will be no further updates or releases, however you can still download the last available version on this page below, and continue using it for as long as you like.
Key featuresDeep Packet Inspection, or just Packet Analysis, uses network packet sniffing to quickly and accurately identify network and application reliability and performance. A network sniffer captures (makes a copy of) the packet data passing through the network. It then analyzes and presents the data to network engineers, system administrators, or anyone who needs a view of traffic passing through their network.
Benefits of Network SniffingWith network sniffing, users can identify the types and volumes of application traffic based on host IP addresses, ports, and protocols in use. This provides a wealth of information that can be very useful to engineers and administrators.
Information from network sniffing includes:
The network sniffer within SolarWinds Network Performance Monitor (NPM) provides a Quality of Experience dashboard that features a quick-glance summary of a variety of network and application performance metrics for all of the configured applications being monitored by network sniffing sensors.
Deploying Network SniffersNPM’s network sniffers can easily be deployed in one of the two following configurations using a simple step-by-step wizard:
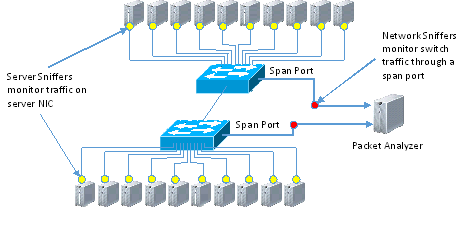
Further information on setting up Network Performance Monitor’s network sniffers can be found in the SolarWinds Network Performance Monitor Administrator Guide.
Additional ResourcesNetwork Performance Monitor Guided Tour
![]() Datasheet: Network Performance Monitor
Datasheet: Network Performance Monitor
![]() Deployment Guide
Deployment Guide
Try SolarWinds Network Performance Monitor for 30 days—no obligation. Test drive our fully functional software and start automating network discovery and monitoring tasks today.
Save Time. Our tools are easy to use and with our simple wizard interface and quick DIY deployment, you’ll be up and running in less than an hour.
Network Sniffer is a tool that can help you locate network problems by allowing you to capture and view the packet level data on your network.
The Colasoft Capsa Network Sniffer is a powerful network analysis tool. It consists of a well-integrated set of functions that can resolve network problems. Colasoft's Network Sniffer can list all of the network packets in real-time from multi-network card (Include Modem, ISDN, ADSL) and can also support capturing packets based on the applications (SOCKET, TDI etc.). You can capture and observe all traffic of the application which is a potential issue. The Colasoft Capsa Network Sniffer GUI eliminates the learning curve and makes it easy to understand and simple to use. The Capsa Network Sniffer has several plug-ins for different protocols such as ETHERNET, IP, TCP, UDP, PPPOE, HTTP, FTP, WINS, PPP, SMTP, POP3 and so on.
What is network sniffer?The work "Sniffer" is a registered trademark of Network Associates, Inc. used on their network analyzing products. Colasoft has spent over 10 years refining it's Capsa Packet Analyzer and sniffer winning awards as an industry leading packet capture and analysis application.
Today, sniffer has become a special name of network monitor and analyzers; it also refers to the collecting of packet level data and information. ISS defines sniffer as: Sniffer is a tool which utilizes network interfaces of computer to capture data packets which destination is other computers.
What is a network sniffer used for?Typical use of network sniffer is to analyze network traffic and bandwidth utilization, so that underlying troubles in the network can be identified. There are, however, two directional usages of sniffer which have coexisted since it was first produced:
Positive usage
Positive usage of a sniffer is also its regular usage, which has as its objective the desire to maintain the network and keep it working normally.
Not all packet sniffing softwares product have the same functions; some sniffers can analyze hundreds of protocols whereas others can only deal with one or two. The most common protocols analyzed by sniffer are TCP/IP, IPX, DECNet-Ordinarily, a sniffer is used as assistant tool of the network engineer for monitoring and analyzing a network, detecting intrusion, controlling traffic or supervising network activity. IT should be noted that such features may also be utilized by hackers as a snooping tool to break into other computers.
Negative usage
Negative usage of a sniffer is well known as its harms to network security:
With more and more hackers using of packet sniffers, it has become one of the most important tools in the defense of cyber-attacks and cyber-crime.
How does a network sniffer work?To understand how a sniffer works, we need to know the main components of a sniffer and its working principles.
Sniffer is a combination of hardware and software. Different sniffers may have various configurations on account of designation and final usage, but basically, a sniffer is composed of four parts:
Most sniffing products can work with standard adapters. Some sniffers only support Ethernet or wireless adapters whereas others support multi-adapters and allow customization. If you plan to install a sniffer on your computer, you shall be sure what type of adapter you have and what type of adapter the sniffer requires.
This is a core component of a sniffer. Each sniffing product has its own drive program, only after completing installation can a sniffer start to capture traffic and data from network.
A buffer is a storage device for captured data from network. In general, there are two modes of buffers: keep capturing until the storage place full, or keep capturing and overflowing as the latest captured data keep replacing the oldest data. The size of a buffer depends on a computer's EMS memory. This means that the bigger the EMS memory is, the more data that can be stored in the buffer.
Capture and analysis are both the most basic and the most important features of a sniffer. Most sniffing products can provide real-time analysis of captured packets, which is the main reason why they are important tools of network engineers. They record the errors and abnormity while they happening.
Some advanced sniffing products (like Colasoft's Capsa Enterprise sniffer) are able to replay the contents of captured packets. These advanced sniffers may even allow you to edit the contents and retransmit the packets to the network.
As a rule, all network interfaces on a segment have the ability to view all of the data transmitted on physical medium and each network interface is supposed to have a hardware address which is different to other existing network interfaces' on network. Every network should have at least a broadcast address. In common cases, a legal network interface should respond to only these two kinds of frames:
When a local network interface card is set in promiscuous mode, this network interface card has a broadcast address and produces a hardware halt to each frame it meets in order to notify the system to deal with every packet passing through.
Each machine on a local network has its own hardware address which differs from other machines'. When a packet is sent, it will be transmitted to all available machines on local network. Owing to the shared principle of Ethernet, all computers on a local network share the same wire, so in normal situation, all machines on network can see the traffic passing through but will be unresponsive to those packets which do not belong to them by just ignoring them. However, if the network interface of a machine is in promiscuous mode, the NIC of this machine can take over all packets and frames it receives on network, namely this machine (involving its software) is a sniffer.
How to find a network sniffer?It is very hard to detect whether there is a sniffer on your network for its activities are quiet though powerful. Sometimes no any trace may be left for you to determine the presence of a sniffer. There are some ways may help you:
There isn't an effective solution which can be used to defend against the sniffer's installation and attack on your system. Network administrators will have a lot to do if they want to reduce the harm from a sniffers. The most popular means are as follows:
To date with the cost and price decreasing, a managed switch has become a main sniffer defense tool both effective and economic.
Encrypting your data can reduce the effects of sniffer to access your private information. A sniffer can capture all data but it can-not decode and read encrypted data.
SSH is a kind of protocol offering secure communication for application programs, based on client/server mode. The distributive port of SSH server is 22, and links are built on RSA method. When authorization complete, data transmitting will be encrypted with IDEA technique, which is quite powerful generally.
F-SSH is the higher level of SSH, usually used by military communication. It offers the most powerful encryption for all purposes. That means if F-SSH is used on a site point, username and password will be not very important. At present, F-SSH is still the most advanced encryption and no one can pierce into it.
Initially presented by Netscape Corporation, SSL's ability to transmit encrypted data on Internet and has been applied widely. SSL provides services from three aspects:
Except above encryption techniques, there are some other tools you can try, like Kerberos, Deslogin, VPN, SMB/CIFS, and the like.
S/key and other one-time password techniques make it insignificant to sniffer account information. S/key bases on the principle that a remote host has gained a password which will not be transmitted on insecure network, a user will get a "challenge" message when connecting the remote host and correct "response" will not appear until the user operates the challenge message and password with a certain arithmetic method. The secure feature of S/key is that passwords do not need to be transferred on network and same "challenge/response" can appear only once.
Another popular one-time technique is ID cards. Each authorized user has an ID card which can bring forth the number codes for visiting personal data. Without this ID card, nobody can decode the number.
A Sniffer can work only in promiscuous mode, so it is crucial whether your system is in such mode or not. In the past, most network interface cards of DOS compatible computers did not support promiscuous mode but now it is the reverse. You shall enquiry system provider about the mode of your network interface.