






 Рейтинг: 4.9/5.0 (1909 проголосовавших)
Рейтинг: 4.9/5.0 (1909 проголосовавших)Категория: Windows: Анализ логов
Small Syslog Server - производительный Syslog сервер для ОС Windows. Позволяет принимать события от ОС брандмауэров, коммутаторов, маршрутизаторов, модемов и т.д. Экспорт событий в TXT формат. Хранит все события в базе SQLite.
Отзывы о Small Syslog Server 5.1 The Bat! Home
The Bat! Home
 Ashampoo WinOptimizer
Ashampoo WinOptimizer
 Mozilla Firefox
Mozilla Firefox
 CheMax Rus
CheMax Rus
 Virtual DJ
Virtual DJ
 Pidgin (Gaim)
Pidgin (Gaim)
 Process Explorer
Process Explorer
 Русская Рыбалка
Русская Рыбалка
Syslog Watcher can collect, parse, store and analyze syslogs from:
Syslog Watcher stores the syslog messages in a special storage. It is a specially optimized type of database. The syslog storage is designed by taking into account the specific requirements of syslog server.
The diagram below shows the positive performance of the program. Syslog Watcher provides a comfortable work environment while displaying up to a million syslog messages.
Significant Advantage - Smart Syslog ParsingThe vendors of devices and program developers often do not follow the RFC3164 standard. In other words, syslog messages that a syslog server receives may not be correctly recognized based only on the specification. Especially, frequent cases have a non-standard format of the date and additional tag (e.g. origin-id).
Our pride is in the intellectual parser of syslog content. This syslog parser attempts to determine the type of syslog source and correctly handle many deviations from the standard.
We are constantly working to improve it. If you suppose that Syslog Watcher does not parse syslog from your sources correctly, please send us examples, and we will add support for it.
Kiwi Syslog ® Server is an affordable, easy-to-use syslog server for IT administrators and network teams. Easy to set up and configure, Kiwi Syslog Server receives, logs, displays, alerts on, and forwards syslog, SNMP trap, and Windows ® event log messages from routers, switches, firewalls, Linux ® and UNIX ® hosts, and Windows ® machines.
Key Features Kiwi Syslog Server Guided Tour Customer TestimonialsTelecom Administrator,
Holy Cross Energy
“This product makes managing my devices much more efficient. It also allows me to proactively prevent system outages.”
Michael G, Online Review
“I use the syslog viewer on a daily basis to monitor any changes in our infrastructure. It proves invaluable and it is my first line of defense. It has saved us numerous times.”
“I use Kiwi Syslog Server, along with the Kiwi Log Viewer nearly every day. It is an invaluable tool for diagnostics and I could never do my job as efficiently without it.”
Jason D. Online Review
Когда вы настроили свою сеть и все у вас работает на ура, то возникает необходимость как то отслеживать все происходящее в ней. Вдруг что-то происходит, а вы и не в курсе :). Для этого я и хочу сегодня рассказать об установке и настройке программы мониторинга Kiwi Syslog Daemon.
Кто заинтересовался, добро пожаловать под кат…
Данная программа предназначена, в первую очередь, для сбора syslog сообщений от устройств и дальнейшего оповещения администраторов о выбранных, по критериям, событиях. Так же она очень полезна для анализа и разбора сбойных ситуаций по полученным сообщениям.
Итак, для установки нам потребуется непосредственно сама программа (я буду использовать Kiwi Syslog версии 8.3.48 (если кому надо, пишите, поделюсь :))) и свободный сервер (я буду использовать Windows Server 2003).
Схема, которую будем собирать, выглядит следующим образом:
На схеме мы имеем три сетевых устройства (два роутера и ASA). Сервер Syslog находится в сети 3.3.3.0/24 и имеет IP-адрес 3.3.3.15. Все устройства мы настроим на отсылку syslog сообщений на этот сервер.
Если у вас в сети до расположения сервера будут находиться устройства безопасности, то не забудьте открыть порт UDP 514 для прохождения сообщений.
Итак, приступим к установке Kiwi Syslog Daemon. Заходим на windows server 2003 и запускаем установочный файл программы:
Принимаем лицензионное соглашение:
Здесь, если вы не хотите каждый раз запускать программу вручную при перезагрузке сервера, то выбирайте пункт инсталляции Kiwi Syslog Daemon в качестве сервиса. Нажимаем «Next»:
Если вы устанавливаете программу, находясь на сервере под локальным администратором, то оставляйте тут настройки по умолчанию. Если же вы находитесь на сервере под каким-то другим пользователем, то вам необходимо указать имя и пароль администратора, входящего в группу локальных администраторов. Нажимаем «Next»:
Здесь, в принципе, можно оставить все по умолчанию. Нажимаем «Next»:
Тут выбираем папку для установки программы и нажимаем «Install». Начнется не длительный процесс установки. В итоге перед вами должно появиться вот такое финальное окно:
Нажимаете кнопку «Finish» и у вас запустится Kiwi Syslog Daemon. Выглядеть окно программы должно следующим образом:
Итак, программа работает. Оставим пока все как есть и перейдем к настройкам наших сетевых устройств. По умолчанию, Syslog будет принимать все syslog сообщения от всех устройств и показывать их в основном экране (Display 00 (Default)).
По очереди заходим на наши устройства и делаем нехитрые настройки.
Enter configuration commands, one per line. End with CNTL/Z.
R2(config)#hostname Router_2
Router_2(config)#int fastEthernet 0/0
Router_2(config-if)#ip address 1.1.1.1 255.255.255.252
Router_2(config-if)#no sh
Router_2(config-if)#exit
Router_2(config)#int loopback 0
Router_2(config-if)#ip address 20.20.20.20 255.255.255.255
Router_2(config-if)#exit
Router_2(config)#logging host 3.3.3.15 – прописываем IP-адрес Syslog Server-а ;
Router_2(config)#logging source-interface loopback 0 – указываем под каким именем (IP-адресов) будет видно устройство на сервере ;
Router_2(config)#logging trap debugging – выставляем уровень сообщений, которые будут отсылаться (в данном случае все сообщения) ;
Router_2(config)#enable secret ciscocisco
Router_2(config)#username admin password cisco
Router_2(config)#line console 0
Router_2(config-line)#login local
Router_2(config-line)#exit
Router_2(config)#line vty 0 15
Router_2(config-line)#login
Router_2(config-line)#login local
Router_2(config-line)#exit
R1(config)#hostname Router_1
Router_1(config)#int fa 0/0
Router_1(config-if)#ip address 1.1.1.2 255.255.255.252
Router_1(config-if)#no sh
Router_1(config-if)#exit
Router_1(config)#int fa 0/1
Router_1(config-if)#ip address 3.3.3.2 255.255.255.0
Router_1(config-if)#no sh
Router_1(config-if)#exit
Router_1(config)#int loopback 0
Router_1(config-if)#ip address 10.10.10.10 255.255.255.255
Router_1(config-if)#exit
Router_1(config)#logging host 3.3.3.15
Router_1(config)#logging source-interface loopback 0
Router_1(config)#logging trap debugging
Router_1(config)#enable secret ciscocisco
ciscoasa(config)# hostname ASA
ASA(config)# command-alias exec wr copy run disk0:/.private/startup-config
ASA(config)# int ethernet 0/1
ASA(config-if)# ip address 3.3.3.1 255.255.255.0
ASA(config-if)# nameif inside
INFO: Security level for "inside" set to 100 by default.
ASA(config-if)# no sh
ASA(config-if)# exit
ASA(config)# enable password ciscocisco
ASA(config)# username admin password cisco privilege 15
ASA(config)# logging host inside 3.3.3.15 – указываем адрес Syslog Server-а и интерфейс, за которым он находится ;
ASA(config)# logging trap informational – выставляем уровень сообщений ;
ASA(config)# logging enable – включаем логирование (не забудьте этого сделать, так как, по умолчанию, без этой команды logging не включится) ;
ASA(config)# wr
Ну что, теперь можно перейти на Syslog Server и посмотреть, есть ли там сообщения от наших сетевых устройств:
Итак, сообщения принимаются и отображаются. Но, во-первых, когда они складываются и отображаются все вместе, это не совсем удобно и наглядно. Во-вторых, при получении, какого либо важного сообщения от устройств, хотелось бы знать об этом. Не заходить же каждую минуту на сервер или сидеть перед монитором и наблюдать. Ну и, в-третьих, нужно иметь файлы, в которые и будут записываться сообщения (так сказать в формате *.txt).
Для устранения всех этих «НО» перейдем на сервер Kiwi Syslog Daemon и начнем пошаговую настройку самой программы, для облегчения нам жизни в дальнейшем :).
Начнем с распределения экранов для отображения сообщений. Каждому устройству определим свой экран и настроим, чтобы в нем отображались сообщения, принадлежащие только соответствующему устройству. Для этого нам необходимо создать три правила (Rule), создать и настроить фильтр и действия.
По умолчанию у нас уже работает правило Default. Изменим ему имя и создадим фильтр, согласно которому в соответствующем экране будут отображаться нужные нам сообщения. Заходим на сервер, открываем программу и переходим, как показано на рисунке:
Откроется окно настроек. Для начала, давайте определим имена наших экранов отображения. Для этого переходим в пункт «Display»:
Здесь, из выпадающего меню выбираем экран (1), присваиваем ему название (2), нажимаем «Update» (3) и изменения должны вступить в силу. Для каждого из экранов можно задать свои параметры (например, мигать при получении сообщения (4), автоматически подстраивать ширину колонки (5) и так далее). Создаем, таким образом, 3 экрана, затем нажимаем «Apply» и переходим к настройкам правила по умолчанию (Default). Изменим, для начала, ему название. Кликнете по названию «Default» правой клавишей мыши и выберете пункт «Rename rule»:
Пишем новое название, нажимаем ввод. Название поменяется. Дальше, давайте создадим и настроим фильтр, чтобы согласно этому правилу на заданном экране отображались сообщения, приходящие только от Router_1. Для этого, кликните правой клавишей мыши на пункте «Filters» и выберете «Add filter»:
Откроется окно настройки нового фильтра:
Здесь из выпадающего меню «Field» (1) выбираем «IP address» (конечно вы можете выбрать и другие параметры), из меню «Filter Type» выбираем «IP Range» (2). После этого, указываем интересующий нас IP-адрес роутера Router_1 (3) (так как у нас IP-адрес один, то начальный и конечный адреса у нас одни и те же). Нажимаем «Apply» (4). Можно также изменить название фильтра (удобно в названии писать, что это за фильтр). Для этого кликните по нему правой клавишей мыши и выберете пункт «Rename filter».
Все, с фильтром закончили. Теперь проверим действия «Actions» для этого правила и, если потребуется, подкорректируем их. На данный момент у нас есть два действия, а именно:
Проверьте, чтобы «Display number» соответствовал вашему правилу. Выберете его из выпадающего списка, затем нажмите «Apply». Теперь, кликните по второму действию «Log to file»:
По умолчанию, все сообщения записываются в файл «SyslogCatchAll.txt», что не совсем удобно. Лучше создать для каждого устройства свой лог файл. Для этого нажмите на кнопку (1), откроется путь к папке, где будут лежать файлы. Пропишите название отдельного файла для устройства (2) и нажмите на «Save» (3). Затем проверьте путь в строке и, если он прописался как надо, то нажмите «Apply».
Все, одно правило для Router_1 готово. Теперь надо создать еще правила для остальных устройств. Для этого кликните правой клавишей мыши по пункту «Rules» и выберете «Add rule». Далее все как мы разбирали выше. Добавьте и настройте фильтр (filter) и действия (Actions). Добавлять действия тоже не сложно (правая клавиша мыши на «Actions», выбираем пункт «Add action» и так далее). Для ориентира, вот картинка:
Создайте остальные правила. В конечном итоге, согласно нашей схеме, у вас должно получиться, что-то вроде этого:
by David Davis [Published on 18 July 2013 / Last Updated on 18 July 2013 ]
This article takes a look at what you need to know about syslog and how to configure your Windows Servers to send syslog.
IntroductionAre you a Windows Admin who doesn’t know a lot about syslog? That’s pretty common as Windows Servers use “events”, not the IETF standard RFC3164 and RFC5424 syslog. Still, the Windows OS can use syslog if taking the right steps. Here’s what you need to know about syslog and how to configure your Windows Servers to send syslog.
What is Syslog?An industry-standard standard system log reporting system, syslog, is used by most devices and operating systems in the datacenter. It includes messages related to systems management, security, debugging, and OS or application errors. Not only is syslog supported by all Linux and Unix-based operating systems but it is also supported by network devices (like routers, switches, and firewalls), storage devices, and even devices like printers. Because of its wide adoption, syslog is a great way to consolidate logging data from across the datacenter in a single place both for preservation and analysis. Analysis of syslog data is critical for security auditing, troubleshooting, and identifying misconfigurations. However, in many cases it is even useful for troubleshooting storage configurations, storage security, and even storage performance. Many devices in the datacenter (such as Cisco routers and switches) do not store historical syslog messages and, thus, it is crucial to consolidate them. If that syslog data is lost when the router looses power or crashes, it may be difficult or impossible to troubleshoot the issue with the device.
With syslog, every device sending syslog messages uses an agent to do so. Those messages from the agents are sent to a central syslog server. Every syslog message is sent with a particular “facility code”, used to identify the type of software that generated the message. Default syslog message are - auth, authpriv, daemon, cron, ftp, lpr, kern, mail, news, syslog, user, uucp, local0 - local7. Those messages are assigned a severity using one of the following classifications - Emergency, Alert, Critical, Error, Warning, Notice, Info, or Debug. In Linux, the syslog messages are usually stored in /var/log and most Linux operating systems offer a command line tool to send data to the log file called logger .
Syslog and the Windows Server OSSo what does all this have to do Windows Server 2012, you ask? With most other devices in the datacenter sending syslog messages to a centralized syslog server, what about Windows? The problem is that, unlike Linux, the Windows OS doesn’t include a syslog agent that is capable of sending syslog data to a syslog server. Without a syslog agent, not only can’t the Windows OS send syslog messages to a syslog server but it also can’t send syslog messages from any applications running in the Windows OS (like a web server or database).
I discovered this while testing the new syslog consolidation and analysis tool from VMware – vCenter Log Insight. Log Insight is a syslog server that performs not only consolidation but also real-time analysis of any logging data sent to it. It’s ideally suited for VMware vSphere virtual infrastructure as it connects directly to your vCenter server and ESXi hosts. It understands the statistics that it collects from the vSphere infrastructure and is a great tool for analyzing system logs and identify errors before they affect end users.
Syslog Agent Options for Windows 2012If you use your favorite search engine and you do a search for “windows syslog agent”, you’ll get number of syslog agents to choose from (most of them being free). Here are some of the options that I found:
Please note:
I did not test any of these syslog agents except for one – Datagram SyslogAgent – (which happened to be the first one that I picked and tested below). Thus, I’m not saying that the one I selected was better or worse than the others, it just happened to be the one I used.
Also note that you shouldn’t confuse syslog servers with syslog agents. Syslog servers (or syslog hosts) collect syslog data and agents send that data. For Windows Server, you need an agent, not a collector (or server). For example, Solarwinds syslog server (formerly Kiwi syslog server) is a syslog server, not a syslog agent. If you don’t have a syslog server already, then that is a good option for general use or vCenter Log Insight is a good option if you are already using VMware vSphere.
Downloading and Installing Datagram Syslog AgentFor my testing, I selected the free Datagram SyslogAgent. From the product page, I clicked the Download and then selected the Datagram Syslog Agent 64-bit download (don’t choose the Syslog Server at the top of the page). Note that you can either go to this webpage directly from the server where you want to install the syslog agent on or you can download it on your local computer and then transport it the Windows server via the network or USB key.
If you extract the 2MB Syslog file that you downloaded, there are a few files but the only three important files are the PDF user’s manual, the SyslogAgent configuration tool, and the SyslogAgent that you need to install on the server.
Figure 1: SyslogAgent Installation Files
In the sense of a traditional Windows application install, there is not one for the SyslogAgent service. You just run the SyslogAgentConfig tool and click Install under the Service Status section at the top.
Figure 2: Installing the SyslogAgent Service
This will create the Windows service for the SyslogAgent.
Before you get too excited and start the service, let’s first configure it.
The minimum configuration would be:
To select where the log data from your Windows host will be sent, enter the IP address of the syslog host, as you see in the graphic, Figure 2, above. In my case, the Log Insight syslog server’s IP address was 10.0.1.120 and we were using UDP port 514.
With this enabled, I checked the Event Logs option and selected what type of event logs I wanted. For system monitoring, I would recommend sending “system logs” but you are welcome to send any type of logs you want such as security logs for
auditing purposes.
Figure 3: Selecting the Event Logs to Send to the Syslog Host
Optionally, you can configure the application log events to forward and even customize their facility and severity, as you see in Figure 4.
Figure 4: Customizing Facility and Severity
Optionally, you can choose to send events from specific Windows applications to the syslog host, even specifying the executable for the custom application (as you see at the bottom of Figure 2).
Once you’ve got it configured, click Start Service .
You are welcome to double check your Windows services to see that the SyslogAgent is added and running as you see below in Figure 5.
Figure 5: SyslogAgent Running in Services
With the syslog agent running, let’s go check our syslog server to see if it is receiving messages from our Windows 2012 Server.
Testing Syslog with VMware vCenter Log InsightLet’s assume that your syslog server was installed and is running fine, at the IP address you specified on the agent. In my case, I am using the new VMware vCenter Log Insight as my syslog host but there are numerous options.
Over on the vCenter Log Insight console, indeed, I was quickly able to identify syslog traffic coming from my Windows 2012 Server (with a DNS name of HV1 ).
Figure 6: Windows Server Syslog Message on vCenter Log Insight
The graphic shows that the syslog server is reporting administrative user logins and logouts (at least in this part of the log) – something that would be very valuable for security audit purposes. Keep in mind that the syslog entries from Windows won’t just be security info. They’ll contain important system and application events as well.
PRTG Network Monitor is a syslog server for Windows: one of the more than 200 sensor types supported by PRTG is the Syslog Receiver: it receives syslog messages from network devices and checks their content and severity.
An alert can be triggered depending on the content and severity of the syslog message. This way, PRTG is a central syslog server which collects the log information of your network devices and informs you when certain events occur. Administrators can define for which types of events they want to receive alerts or warnings. This way, PRTG makes sure that you will not overlook important information.
As part of its flexible alerting system that supports various notifications technologies (e.g. email or SMS, or executing an external program), PRTG also offers the possibility to send SNMP traps and syslog messages to notify administrators of alerts.
You can define which messages you want PRTG to process by defining filters in the sensor settings. This way you can monitor only data which you are interested in and PRTG will purge not needed data. For example, you can create a filter for messages that have to "Include" specific parameters, or you do not want to process certain messages and "Exclude" specific parameters. The received data is stored in an internal high performance database and available on your respective probe system as common files (one file is created per hour) as well as directly on PRTG's web interface.
You can individually define which types of messages will be considered as a "Warning" or "Error". For example, let a message with a severity of 4 switch the sensor into a Warning status, and all severities below into an Error status. This way, you get an alarm immediately depending on your needs.
Download the Syslog Server for WindowsDownloading and installing PRTG only takes a few minutes. The network monitor runs on all Windows versions (XP or later). An install wizard takes you through the straightforward installation process, and with auto discovery, your sensors can start monitoring your network in a matter of minutes. Download the trial version now and collect and analyze the information of your managed devices in one place.
Free Trial
No limitations for 30 days Freeware Download
100 Sensors - Full Functionality
PRTG - More Than a Syslog Server for WindowsSyslog is a way for network devices to send event messages to a logging server – usually known as a Syslog server. The Syslog protocol is supported by a wide range of devices and can be used to log different types of events. For example, a router might send messages about users logging on to console sessions, while a web-server might log access-denied events.
Most network equipment, like routers and switches, can send Syslog messages. Not only that, but *nix servers also have the ability to generate Syslog data, as do most firewalls, some printers, and even web-servers like Apache. Windows-based servers don’t support Syslog natively, but a large number of third-party tools make it easy to collect Windows Event Log or IIS data and forward it to a Syslog server.
Unlike SNMP. Syslog can’t be used to “poll” devices to gather information. For example, SNMP has a complex hierarchical structure that allows a management station to ask a device for information on things like temperature data or available disk space. That’s not possible with Syslog – it simply sends messages to a central location when specific events are triggered.
Syslog ServersSyslog is a great way to consolidate logs from multiple sources into a single location. Typically, most Syslog servers have a couple of components that make this possible.
We won’t go in depth on Syslog messages here, but there are a few important things to know.
Syslog messages usually include information to help identify basic information about where, when, and why the log was sent: ip address, timestamp, and the actual log message. Messages are sometimes in a descriptive, human-readable format – but not always!
Syslog uses a concept called “facility” to identify the source of a message on any given machine. For example, a facility of “0” would be a Kernel message, and a facility of “11” would be an FTP message. This dates back to Syslog’s UNIX roots. Most Cisco network equipment uses the “Local6” or “Local7”facility codes.
Syslog messages also have a severity level field. The severity level indicates how important the message is deemed to be. A severity of “0” is an emergency, “1” is an alert that needs immediate action, and the scale continues right down to “6” and “7” – informational and debug messages.
The Downsides to SyslogThere are a few downsides to Syslog.
First, the problem of consistency. The Syslog protocol doesn’t define a standard way for message content to be formatted – and there as many ways to format a message as there are developers. Some messages may be human readable, some aren’t. Syslog doesn’t care – it just provides a way to transport the message.
There are also some problems that arise because of the way syslog uses UDP as a transport. UDP is connectionless and not guaranteed – so it could be possible to lose log messages due to network congestion or packet loss.
Finally, there are some security challenges with syslog. There is no authentication on syslog messages, so it could be possible for one machine to impersonate another machine and send bogus log events. It is also susceptible to replay attacks.
In spite of this, many administrators find that the syslog is a valuable tool, and that the downsides are relatively minor.
As you can see, Syslog can be a powerful tool that can make it easier for administrators to manage complex networks. But one of the biggest challenges with Syslog is the volume of data. The logging server software must simplify log management, and help admins filter and focus on messages that truly matter. In a future post, we’ll show you some tools that you can use to get the most out of the Syslog.
In the meantime, check out our reviews of network management systems that also have syslog capabilities, like ManageEngine’s OpManager. SolarWinds Orion NPM. or OpenNMS .
Michael Pietroforte is the founder and editor of 4sysops. He is a Microsoft Most Valuable Professional (MVP) with more than 30 years of experience in system administration.
The Wikipedia says that Syslog is the de facto standard for logging program messages. Well, let’s say, it is the most common logging protocol outside the Windows world. If you also administer Linux boxes, then you know that the Open Source OS still uses plain text files for logging OS and application messages. To keep track of all log files, Linux admins often use the Syslog protocol to collect all log data at a central location. Moreover, Syslog is also supported on Macs, other UNIX systems, and Syslog-capable network devices. Thus, if you want to manage all your logs with one system, it makes sense to introduce Syslog in your network.
Since Windows doesn’t support Syslog natively, you have to install third-party software. You need a Syslog agent (client) on every machine where you want to collect Windows event log messages and, at least, one Syslog server where all the data comes together. Jeff submitted a free Syslog client for Windows a few days ago. So, I thought, we should also have a free Syslog server in our collection of free log management tools. SolarWinds’ Kiwi Syslog Server is probably the most popular free Syslog “daemon” for Windows.
If you want to play a little with Syslog, you can install the Kiwi Syslog Server and the CorreLog Syslog Client on the same Windows machine. It doesn’t have to be a server. You must install the Kiwi Syslog Server first because the client can’t be installed without specifying the server.
Configuring the Syslog client ^To get an idea of how Syslog works, launch the CorreLog Windows Syslog Agent Configuration with admin privileges and then open its config file from there. For testing purposes, you can change the DefaultSeverity parameter in the section for the Security Eventlog from “disabled” to “auto,” which means that all messages in the Windows security event log will be sent to the Syslog server. If you skim over the CorreLog Syslog configuration file, you will understand how you can send only those event log messages that are of interest to you. Most important is the MatchKeyword directive which allows you to restrict messages to certain keywords. The CorreLog Syslog Agent comes with documentation that explains all directives well.
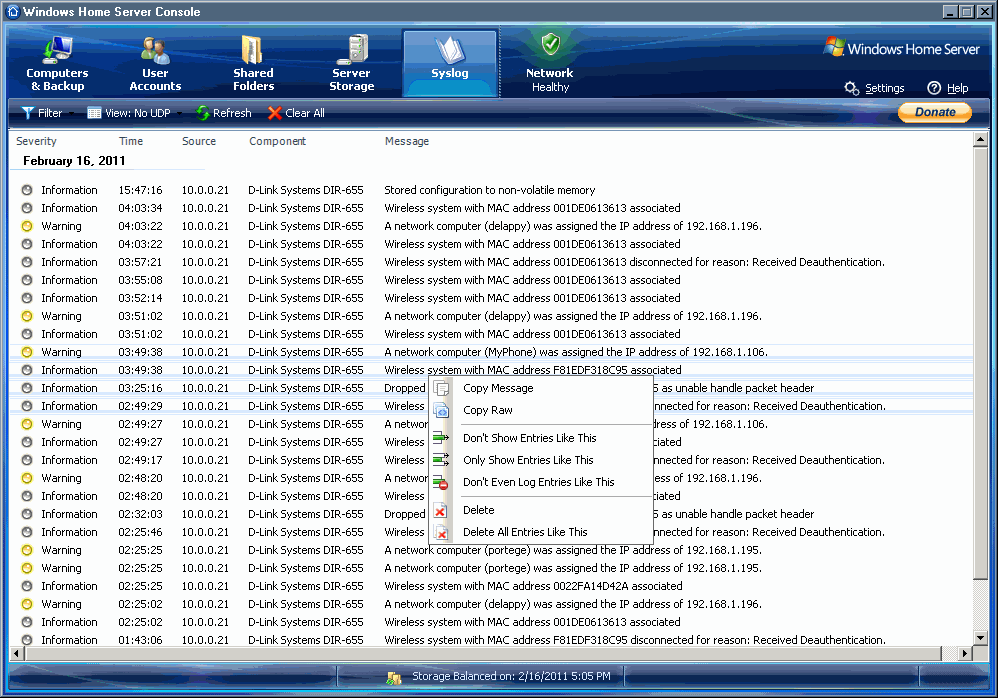
If you now change the password of a Windows user on your test machine, you should receive a new message on the Kiwi Syslog Server. I think, you got the picture now of how Syslog works. On the client, you configure the type of messages you want to send to the server, and on the Syslog server collect all the data. In addition, you can specify rules on the Syslog server that will trigger actions when messages of a certain type arrive.
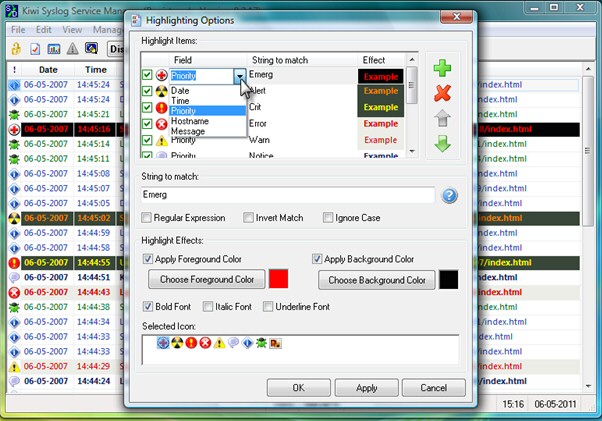
Configuring the Kiwi Syslog Server ^To configure rules, open Setup on the Kiwi Syslog Server Console. In the Rules section, you can define filters and actions. Filters of the free edition are priority, time of the day, and input source (UDP, TCP, SNMP, keep alive). The actions are triggered when a message makes it through the filter. The full version of Kiwi Syslog Server supports 15 different actions, whereas the free version supports only 6: display (10 different displays), log to file, sound, forward to another host, send SNMP trap, and stop processing.
After you install Kiwi Syslog Server, you can test the licensed edition for 30 days. After 30 days, all features that are only available in the licensed version are disabled and you will see a red message at the bottom of the setup window if you try to access one of these features. A comparison of the free and the licensed full versions can be found here .
I didn’t cover all features of Kiwi Syslog Server 9. It is certainly a powerful free Syslog server for Windows. However, if your network is mostly a Windows shop, then tools such as GFI EventsManager or Netikus.net EventSentry are probably better choices because they allow you to leverage the full power of the Windows event log system. Both tools support the Syslog protocol. EventSentry is also available as a free version .