
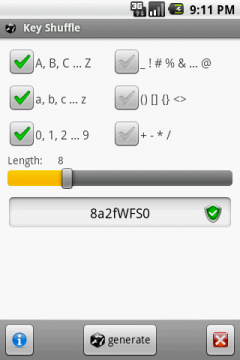








 Рейтинг: 4.7/5.0 (1687 проголосовавших)
Рейтинг: 4.7/5.0 (1687 проголосовавших)Категория: Android: другое
PHP is a popular programming language often used to create applications with web-based interfaces. In fact, much of the Internet and Web runs on PHP!
Part of what initially fuelled PHP's popularity among software engineers and web developers is that PHP comes with a rich and useful set of built-in libraries, procedures, functions, and classes that provide all sorts of functionality often needed when creating applications with web-based interfaces (saving you the time of creating these things yourself). One of these useful built-in procedures is the PHP shuffle() procedure.
PHP's shuffle()The PHP shuffle() procedure shuffles what's in an array, putting them in random order. Let's illustrate what it does with an example:
The output from this might look like:
(Note that I said "might look like" because PHP's shuffle() procedure reorders the contents of the array in random order. Thus, I won't know exactly what reordering PHP's shuffle() procedure will put the array in when you call it.)
Problem with PHP's shuffle()One of the problems with PHP's shuffle() procedure is that it does not preserve an array's keys! That behavior makes sense when your array has numeric keys (i.e. 0, 1, 2, 3, 4. ) but might be problematic for you if you, for instance, have an array with string keys (and want to preserve those string keys in the shuffled array).
Let's illustrate this with an example:
Your output might be:
Note that the keys of the shuffled array are different! In fact, the original keys are gone! replaced by numeric indexes. Sometimes, this may be a problem!
For example, you may have wanted the shuffled array to preserve the keys and look like this:
PHP's shuffle() procedure does NOT support this, unfortunately. However, with the procedure I provide (which I call shuffle_assoc() ) you can shuffle an array while preserving the keys.
shuffle_assoc()Here's the code for shuffle_assoc() ; a function, similar to PHP's shuffle() procedure, but which preserves the original array's keys:
shuffle_assoc() ExampleCreate Keyed Invertible Substitutions A Ciphers By Ritter Page Terry Ritter
Many modern ciphers are based on keyed invertible substitution tables. Each such table contains exactly the same values as any other, but in a different order. In this environment, keying consists of constructing a particular arrangement of the data in each table. Ideally, every possible arrangement or permutation would be equally likely.
Separating the keying system from the actual ciphering allows the ciphering core to be as simple and fast as possible. This separation also allows each system to be analyzed largely independently.
Keying System OverviewThe goal of the keying system is to construct arbitrary invertible tables under the control of a key. In a sense, the arrangement of values in each table is the "real" key for the cipher. The keying system simply processes the external key into the larger internal form required by the design.
This key processing can be accomplished by using the external key to set the initial state for a random number generator (RNG), then using the RNG to shuffle the tables. Here we also use an intermediate RNG which expands the data and provides nonlinearity in the original state of the keying RNG, which helps protect against attack.
It is first necessary to convert an external key of arbitrary content and length into the fixed amount of data suitable for initializing a serious RNG. The general name for this process is hashing. By including hashing as part of the cipher, we can directly handle text keys, binary keys, voice keys, picture keys, file keys, or keys based on any information whatsoever, and of arbitrary size. And if we want a weaker cipher, we can just agree to use short external keys.
The hash result is used as the state or "seed" for the first RNG. The pseudo-random sequence from the first RNG is filtered to make it nonlinear and stronger, and the resulting sequence is used to construct the state for the second RNG. The second RNG produces a pseudo-random sequence which is also nonlinearly filtered. The resulting sequence is used to shuffle the tables.
The Hashing SubsystemWe wish to use a first RNG having 31 elements of 32 bits each, so it is convenient to develop a hash result of 992 bits from the variable-size key. For a hash of this size, we use conventional cyclic redundancy check (CRC) technology with a set of 32 different degree-31 mod-2 primitive polynomials.
Unlike ad hoc cryptographic hash functions, CRC is well understood and has a strong mathematical basis. (For an introduction, see Ramabadran and Gaitonde [5 ]; CRC is also mentioned in Sect 5.3 of Ritter [6 ].) Although CRC is a linear function, and thus contributes no added strength, it is here used only for key processing, so no added strength is needed or wanted.
Each CRC scan across the key uses a particular degree-31 polynomial, and produces a 31-bit result in a 32-bit element. So by performing 32 different CRC's using each of 32 different polynomials, we accumulate 32 results, each of which has a most-significant-bit (msb) of zero. We then delete the msb's and pack the 32 elements of 31 valid bits into 31 elements of 32 bits each. This also causes the 32 CRC results to each start at a different bit-position in the packed array.
In our current design, each CRC hashing polynomial has an approximate balance in ones and zeros. These polynomials had to be constructed, because polynomials meeting the balance requirement were not available in the literature. The general ideas behind finding irreducible and primitive mod-2 polynomials are discussed in Ritter [6 ], Sect 6.5. A CRC only needs irreducibles, but at degree 31 these are all primitive anyway.
CRC hashing gives us a way to handle keys of arbitrary content and size, in a fixed, and relatively easily analyzed RNG system. The key can be a text string or a random binary value of arbitrary length. Keys of any reasonable size are thus directly supported in a fixed-size hash machine.
The First RNGWe wish to use some form of RNG to key the ciphering tables. Our published survey of ciphering RNG's [6 ] (Ritter. in particular Sect 4.10 ), revealed the Additive RNG as a very attractive choice. An Additive RNG has a large internal state, a huge proven cycle length, and especially fast operation. It is easily customized by using an appropriate primitive mod-2 feedback polynomial. And -- unlike many cryptographic RNG designs -- an Additive RNG supports almost arbitrary initialization.
The Additive RNG is described in Knuth II [2. 26-31]. Also see Marsaglia [3 ] for comments, and Marsaglia and Tsay [4 ] for a sequence length proof.
We wish to use a deg-31 Additive RNG with 32-bit elements, which thus requires a 992-bit initialization value. We obtain this by hashing the external key into a 31-element array of 32-bit values. (We also scan this array looking for '1'-bits in the least-significant-bit (lsb) of each element; if none are found, the lsb of element [0] is made a '1'.) For best acceptance, the mod-2 primitive trinomial is taken from Zierler and Brillhart [7. 542].
The Jitterizer Nonlinear FilterThe Additive RNG is a linear system; the sequence of values it produces is inherently linearly related. This is a potential weakness, which we avoid in several ways. One way is to use a nonlinear filter which we call a "Jitterizer." (The concept of a Jitterizer was introduced in Sect 5.5 of Ritter [6 ].)
The approach taken here is to "drop" or delete a pseudo-random number of elements from the sequence, then "take" or pass-along another pseudo-random number of elements. Each of the elements in a "take" group is also exclusive-ORed with one of the dropped values.
When called in the "drop" phase, the Jitterizer calls the RNG extra times until the first element of the next "take" phase is reached. This value is offset and returned. When called in the "take" phase, the Jitterizer just calls the RNG once, offsets the value and returns it.
Our current Jitterizer design is constructed to drop 2..5 elements (avg. 3.5), then take 1..16 elements (avg. 8.5). This will drop out almost 30 percent of a long sequence. Each last dropped value becomes a new offset, so the 32-bit offsets change about every 8 or 9 returned values. Each first dropped value is offset, XORed down to a byte, and used to set take and drop counts.
The term "jitterizer" is used as a counterpart to the "synchronizer" mechanisms commonly used in digital design. An oscilloscope display which is not synchronized is said to "jitter." The purpose of a jitterizer is to create a non-synchronized stream.
The Second RNGWe wish to use a deg-127 Additive RNG to control the actual shuffling. Such an RNG has an internal state of 4064 bits, which we originally develop by running the deg-31 RNG until we get 127 Jitterized 32-bit elements. We also scan the resulting state to assure that at least one '1' occurs in the lsb position, and increment element [0] otherwise.
The mod-2 primitive trinomial is again taken from Zierler and Brillhart [7. 542]. The sequence from the second RNG is also jitterized and used to control the shuffling.
The Shuffling SubsystemFirst we initialize the tables in a counting pattern. Then we shuffle the tables. Twice.
The shuffle routine is the standard Durstenfeld [1 ] shuffle described in Knuth II [ 2. 139 §3.4.2.P ] and mentioned in Sect 6.7 of Ritter [6 ].
Suppose we have "byte wide" substitution table, an array of 256 byte elements, from index [0] through [255]: To make a random arrangement, we first select one of the entries by creating a random value on the range 0..255. We then take the value in that element and place it into some known position; it is convenient to place the value at the far end of the array. This leaves us with a empty place in the array, and an extra value which came from the far end. We might shift the second part of the table down to fill the hole and make room for the displaced value, but it is easier to simply put the displaced value in the empty position. This amounts to exchanging the values in the randomly selected position and the end of the array.
With one value positioned, we have 255 values remaining, in positions [0] through [254]. So we use a random value in the range 0..254 to select a position, and exchange the selected value with the value in position [254]. Sometimes these are the same, which is fine. We similarly fill positions [253], [252], etc. down to position [1], which also defines the remaining value in position [0].
Perhaps the hardest part of this process is the development of unbiased random values with the correct range at each step. The Additive RNG's will generate random binary 32-bit values. It is certainly possible to convert the random values to reals on the range 0..1 and then multiply by the current position. Or we could do some sort of scaled integer multiply.
Another approach is to simply get a random value, and if the result is in our desired range we accept it, otherwise we reject it and try again. Now, obviously, the likelihood of getting a value in 0..253 from a 32-bit random value is pretty low, so we first convert the 32-bit value into an 8-bit value by exclusive-ORing high and low halves, twice. Similarly, the likelihood of getting a value in 0..5 from an 8-bit random value is also pretty low, so we arrange to mask the random value in power-of-2 steps. To look for a value in 0..5, we mask the 8-bit random to 3 bits, giving a range of 0..7, so in this case we expect to find a value in our range 6 times out of 8. This approach has the advantage of clearly giving an even probability in each desired range, something which is often not as clear when using reals and scaled multiplies. The approach also skips RNG values occasionally (about 1 time in 4, on average), which adds further uncertainty to the sequence position of each RNG value used.
Strength ArgumentsSince RNG is mainly used to key the tables (it does also develop the few initial values needed by the core), an attack on the RNG can be made only after an Opponent has somehow developed some amount of table content. Note that a single "byte-wide" substitution table (an array of 256 byte values) represents 1648 bits of information.
The external keys are assumed to be unknown, since, if we do not make this assumption, The Opponent can simply enter the correct key and decipher the data directly. These are secret keys and we assume that they have been distributed by some secure process.
We do not particularly care if the mechanism protects the value of the external key, since the state of the ciphering core alone is sufficient to decipher data. An Opponent who can somehow develop the core state has no need for the original key.
We do seek to defend against any ability to use some amount of known state to develop knowledge of additional state. We seek to defend against using the recovered state of one table to develop the content of other tables. We thus assume some amount of known state, and seek to prevent that knowledge from being extended to other entries or tables.
There are basically four levels of resistance in the keying system:These arguments form the basis for an assumption of sufficient strength in the keying system.
References1. Durstenfeld, R. 1964. Algorithm 235, Random Permutation, Procedure SHUFFLE. Communications of the ACM. 7: 420.
2. Knuth, D. 1981. The Art of Computer Programming, Vol. 2, Seminumerical Algorithms. 2nd ed. Addison-Wesley: Reading, Massachusetts.
3. Marsaglia, G. 1984. A current view of random number generators. Proceedings of the Sixteenth Symposium on the Interface Between Computer Science and Statistics. 3-10.
4. Marsaglia, G. and L. Tsay. 1985. Matrices and the Structure of Random Number Sequences. Linear Algebra and its Applications. 67: 147-156.
5. Ramabadran, T. and S. Gaitonde. 1988. A Tutorial on CRC Computations. IEEE Micro. August: 62-75.
7. Zierler, N. and J. Brillhart. 1968. On Primitive Trinomials (Mod 2). Information and Control. 13: 541-554.
Last updated: 1997-08-22
In addition to the left and right hand modules, separated by the center Backspace and Enter keys, the EZR 2030-US contains the following 5 modules (rollover green buttons to expose modules) :
MODULE 1: The A-Z typing module
This is the complete and standard version of the A-Z keypad layout modified into the more logical and ergonomic matrix design, available in Qwerty or Dvorak .
MODULE 2: The left control module
This module contains:
Left Ctrl -Alt -Shift - the main modifiers for keyboard shortcuts
Function – while depressed, all blue-labeled keys are activated
Start – same as Windows key
Apps – same as the other Windows key
Shuffle – toggles between the last two opened applications
• Hold shuffle and use tab to select from all opened applications
MODULE 3: The right control module
This module contains:
Num – locks the Num Pad and alternative cursor keys into activation
Function – duplicate of the lower left Function key
Backspace – duplicate of the Center Backspace key
Delete – located on home row, tactile bump, colored for easy detection
Enter – duplicate for center Enter
Right Ctrl -Alt -Shift -Insert modifiers –
• Shift + Delete = cut
MODULE 4: The cursor control module
This class consists exclusively of static methods that operate on or return collections. It contains polymorphic algorithms that operate on collections, "wrappers", which return a new collection backed by a specified collection, and a few other odds and ends.
The methods of this class all throw a NullPointerException if the collections or class objects provided to them are null.
The documentation for the polymorphic algorithms contained in this class generally includes a brief description of the implementation. Such descriptions should be regarded as implementation notes. rather than parts of the specification. Implementors should feel free to substitute other algorithms, so long as the specification itself is adhered to. (For example, the algorithm used by sort does not have to be a mergesort, but it does have to be stable .)
The "destructive" algorithms contained in this class, that is, the algorithms that modify the collection on which they operate, are specified to throw UnsupportedOperationException if the collection does not support the appropriate mutation primitive(s), such as the set method. These algorithms may, but are not required to, throw this exception if an invocation would have no effect on the collection. For example, invoking the sort method on an unmodifiable list that is already sorted may or may not throw UnsupportedOperationException.
Spark 1.5.2 uses Scala 2.10. To write applications in Scala, you will need to use a compatible Scala version (e.g. 2.10.X).
To write a Spark application, you need to add a Maven dependency on Spark. Spark is available through Maven Central at:
In addition, if you wish to access an HDFS cluster, you need to add a dependency on hadoop-client for your version of HDFS. Some common HDFS version tags are listed on the third party distributions page.
Finally, you need to import some Spark classes into your program. Add the following lines:
(Before Spark 1.3.0, you need to explicitly import org.apache.spark.SparkContext._ to enable essential implicit conversions.)
Spark 1.5.2 works with Java 7 and higher. If you are using Java 8, Spark supports lambda expressions for concisely writing functions, otherwise you can use the classes in the org.apache.spark.api.java.function package.
To write a Spark application in Java, you need to add a dependency on Spark. Spark is available through Maven Central at:
In addition, if you wish to access an HDFS cluster, you need to add a dependency on hadoop-client for your version of HDFS. Some common HDFS version tags are listed on the third party distributions page.
Finally, you need to import some Spark classes into your program. Add the following lines:
Spark 1.5.2 works with Python 2.6+ or Python 3.4+. It can use the standard CPython interpreter, so C libraries like NumPy can be used. It also works with PyPy 2.3+.
To run Spark applications in Python, use the bin/spark-submit script located in the Spark directory. This script will load Spark’s Java/Scala libraries and allow you to submit applications to a cluster. You can also use bin/pyspark to launch an interactive Python shell.
If you wish to access HDFS data, you need to use a build of PySpark linking to your version of HDFS. Some common HDFS version tags are listed on the third party distributions page. Prebuilt packages are also available on the Spark homepage for common HDFS versions.
Finally, you need to import some Spark classes into your program. Add the following line:
PySpark requires the same minor version of Python in both driver and workers. It uses the default python version in PATH, you can specify which version of Python you want to use by PYSPARK_PYTHON. for example:
Initializing SparkThe first thing a Spark program must do is to create a SparkContext object, which tells Spark how to access a cluster. To create a SparkContext you first need to build a SparkConf object that contains information about your application.
The first thing a Spark program must do is to create a JavaSparkContext object, which tells Spark how to access a cluster. To create a SparkContext you first need to build a SparkConf object that contains information about your application.

4 трека на дебютной пластинке группы, которая была записана на "Studio 73" в Копенгагене - единая вращающаяся линия вокруг бесконечной меланхолии и одиночества. Если смешать эту линию с комком энергии и музыкальной жестокостью - вы нарисуете картину этого молодого трио звукового дарка.
The band's sound is built around a combination of raw bursts of energy and monotonous drones. This is supported by a song universe containing noise, desperation and evil from the outmost corners.
The sound emerges from the 60's New Yorker scene, the 80's postpunk, the surf-noir of the B-movies and electrical Americana. Even though much inspiration has been drawn from the metropolitan subgenres, the at times manically repetitive sound universe reflects the more desolate parts of the Danish province.
слушать онлайн или скачать mp3
Все песни «Cevin Key Maniac Shuffle» слушайте бесплатно онлайн на сайте ololo.fm (4 песни)
А также ВСЯ МУЗЫКА интернета — слушайте бесплатно и без регистрации!
 cEvin Key (Kevin Crompton) участник культовых Skinny Puppy, с 95 года играл на клавишах и на электро-ударном комплексе в Download вместе с Anthony Valcic, Ken Marshall, DJ Philth, Marc Spybey и Dwayne Goettel. cEvin Key это один из столпов, живая легенда андерграундной электронной сцены. Артист давно вышел за узкие рамки индустриального жанра и создал свой собственный, уникальный мир сюрреалистических звуков и неземных гармоний. Сегодня его творчество связывают с так называемой экспериментальной электронной волной, с авторским звуковым авангардом, оно интересно и актуально как никогда.
cEvin Key (Kevin Crompton) участник культовых Skinny Puppy, с 95 года играл на клавишах и на электро-ударном комплексе в Download вместе с Anthony Valcic, Ken Marshall, DJ Philth, Marc Spybey и Dwayne Goettel. cEvin Key это один из столпов, живая легенда андерграундной электронной сцены. Артист давно вышел за узкие рамки индустриального жанра и создал свой собственный, уникальный мир сюрреалистических звуков и неземных гармоний. Сегодня его творчество связывают с так называемой экспериментальной электронной волной, с авторским звуковым авангардом, оно интересно и актуально как никогда.
Об исполнителе «Cevin Key» Видеоклипы «Cevin Key» Фотографии «Cevin Key»
Знаете что-то интересное про исполнителя «Cevin Key»? Расскажите нам
 Like the track? Click the [↻ Repost] button! Join the Movement @ EDM.com -------------------------------------------------------------------------- Follow @brandon-zeier http://www.twitter.com/BrandonZeier Follow @pkeys http://www.facebook.com/PKeyss http://twitter.com/pkeys_ Follow Us @ EDM.com www.Facebook.com/edmcom www.twitter.com/TheEDMNetwork www.youtube.com/EDM www.instagram.com/edm plus.google.com/+EDM SC: @EDM -------------------------------------------------------------------------- Send all demos to deepsounds@theedmnetwork.com to have your track featured! --------------------------------------------------------------------------
Like the track? Click the [↻ Repost] button! Join the Movement @ EDM.com -------------------------------------------------------------------------- Follow @brandon-zeier http://www.twitter.com/BrandonZeier Follow @pkeys http://www.facebook.com/PKeyss http://twitter.com/pkeys_ Follow Us @ EDM.com www.Facebook.com/edmcom www.twitter.com/TheEDMNetwork www.youtube.com/EDM www.instagram.com/edm plus.google.com/+EDM SC: @EDM -------------------------------------------------------------------------- Send all demos to deepsounds@theedmnetwork.com to have your track featured! --------------------------------------------------------------------------
mueve el culo man"!
Comment by Michal Bartosik2015/06/26 20:57:22 +0000
Comment by regtheledge@sweatyturtle: its so rare these days!
Comment by JackGladney